In digital landscape, where internet privacy and protection are more important than ever, understanding the role of proxy servers has turned into vital for both personal users and companies similarly. A proxy acts as an intermediary connecting your system and the internet, offering a layer of security and anonymity. This piece will lead you through the crucial aspects of choosing the appropriate proxy to fulfill your requirements, regardless of whether you're looking to improve your online safety, overcome geographic blocks, or optimize your online workflows.
With numerous options available, touring the world of proxy servers can feel daunting. From the variations between various categories such as Hypertext Transfer Protocol, Socket Secure, and transparent servers, to understanding how they can enhance your internet privacy and productivity, we will explore what you should consider when selecting the best proxy for your specific circumstances. Whether you are a gamer aiming to minimize latency or a company seeking improved cybersecurity measures, this thorough manual has got you supported.
Comprehending Proxy Server along with Their Functions
A proxy server functions as an go-between between a user's device and the web, enabling queries and responses. When a user looks to reach a webpage, the call first travels to the proxy instead of of straight reaching the destination site. The intermediary then forwards the call to the target site, retrieves the information, and sends it again to the user's device. This method helps mask the user's internet protocol address, making it more difficult to trace their online activity.
The capabilities of proxy extends further than mere anonymity. They can store information, which enables for quicker access to regularly accessed websites, in the end enhancing efficiency. Additionally, Omeka provide the capability to screen content, preventing access to certain websites based on predefined rules. This feature is particularly beneficial for organizations looking to restrict access to non-business content, consequently promoting output within the environment.
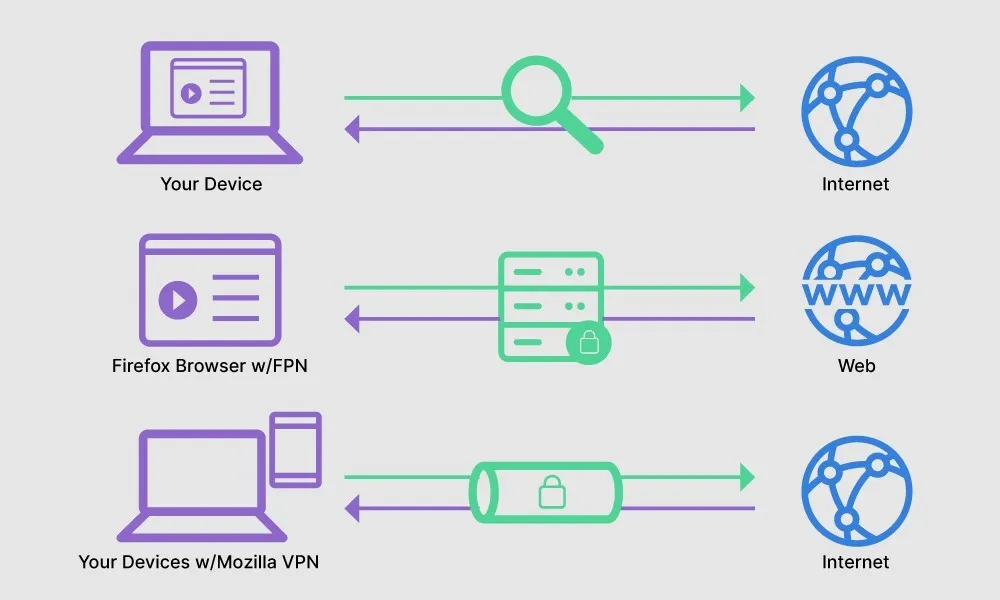
In regards to security, proxy servers can aid lessen threats related to online activities. By functioning as a barrier, they can prevent direct access to critical data and act as a shield against potential hazards such as cyberattacks. Some proxy servers also integrate encryption protocols, providing an added layer of protection for user information as it moves across the network. Overall, understanding how proxies operate is essential for leveraging their benefits in multiple internet uses.
Advantages and Drawbacks of Using Proxy Servers
Utilizing proxy servers offers several benefits that boost online privacy and security. By functioning as intermediaries between users and the internet, proxy servers help to conceal the original IP address, which can protect users from unwelcome tracking and profiling by marketers and malicious entities. This disguise boosts user privacy and can reduce the risk of targeted cyberattacks. Additionally, proxies can also provide access to geo-restricted content, enabling users to bypass censorship and stream services or websites that might otherwise not be accessible in their region.
However, there are risks associated with the utilization of proxy servers, particularly when opting for complimentary or unreliable services. Free proxies can put users to potential data breaches, where sensitive information may be recorded or sold to third parties. Furthermore, many such proxies lack proper security measures, rendering them susceptible to hackers. Users may also face slower internet speeds and connection instability, especially if the proxy server is congested or poorly maintained. It is crucial to carefully evaluate the quality and trustworthiness of a proxy service before investing to its use.
Another crucial factor is the lawful and moral implications of using proxy servers for certain activities. While they can provide considerable advantages for tasks like web scraping or accessing restricted content, improper use may lead to breaches of terms of service and potential legal repercussions. Users should be cognizant of the ethical considerations involved in using proxies, ensuring that they are compliant with all applicable laws and guidelines while taking advantage of the capabilities these servers offer. Weighing the benefits with knowledge of potential downsides is crucial for making educated decisions about proxy usage.
Choosing the Ideal Proxy for Your Needs
As you selecting a proxy, it's important to evaluate the needs. Different tasks frequently demand specific types of proxies. For instance, if you require to reach location-restricted content, a home proxy could be a best choice as it looks like a regular user's network. On the other hand, if you are focused on data scraping or market research, server-based proxies are typically faster and more capable, albeit not as private. Identify the primary intent of your proxy application to make an informed decision.
Another important aspect is the degree of anonymity and safety you desire. When online privacy is a high priority, look for proxies that offer solid encryption and further security options. Some proxies provide anonymity degrees that protect your real IP address is kept hidden, while alternative options may trade off on privacy for speed. Evaluating the balance between these factors based on your needs can help you choose the right proxy solution.
Finally, keep in mind price and reliability. While free proxies might be attractive, they typically come with risks, such as data leaks and inconsistent performance. Spending in a reputable paid proxy service generally delivers better security, quicker speeds, and focused support. Investigate various providers, read testimonials, and take benefit of free trials to find a proxy service that offers the greatest benefit for your needs.
